Shift left in 60 seconds
Shift left is a way to think about security work. It aims to reduce the most risk, for the least effort, and self-improve over time.
Imagine the set of outcomes for any given security risk:
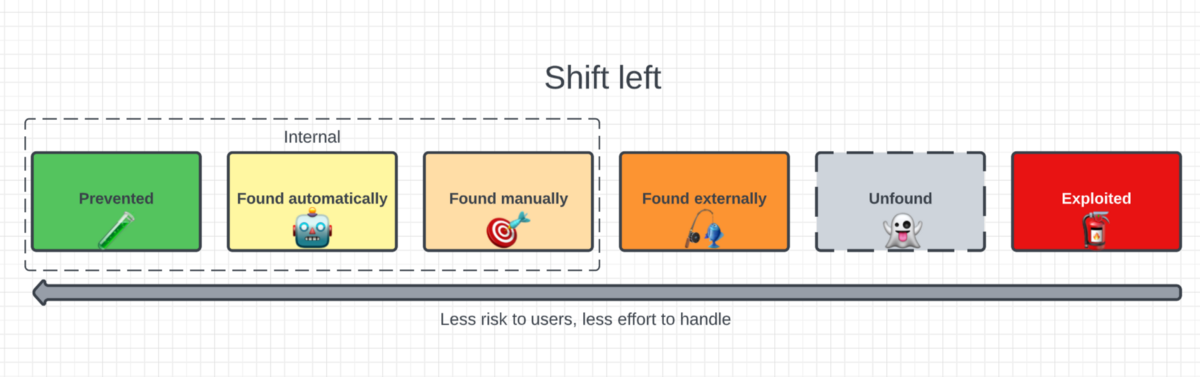
- Prevented — Risk is never materialized
- Found automatically — Risk is found, but time-cheaply by tooling
- Found manually — Risk is found, by people inside the company
- Found externally — Risk is found, and told to the security team
- Unfound — Risk lurks unfound
- Exploited — Risk is found, and exploited by badguys
For the thousands of risks unearthed, we want to tilt the most likely outcomes leftwards on this spectrum, to shift left.
This applies to most (all?) work done by an information security team.
Benefits
- Finding things earlier is better, as less chance of harm to users
- Efficiency — The set of risks possible to prevent remove huge swaths of more expensive work downstream, and risks findable by computers, should be found that way
- Defense in depth — If one method misses a risk, a later method may find it
- Continuous Improvement — Stacking different methods means an inherent feedback loop for each individual method to improve, E.g: A bug bounty finding becomes a new static analysis rule
Measurements
How do we know if its working?
- Classes of security risk eliminated, e.g: sql injection, malware on laptops
- % of security risks found via humans vs automation
- Human time cost per risk found, severity-weighted. A CVE 9 cost 400 hours to find in 2015, and 200 now.
- The distribution of which risks fell into which outcome bucket n years ago vs today, ideally shifting leftward.
- Lessons into landed work. How many new rules/tools/partnerships/training were created from generalizing novel risks found
- Mitigations - 10 classes of risk still happen, but when they do is blast radius smaller? E.g A sandbox for memory safety vulns
